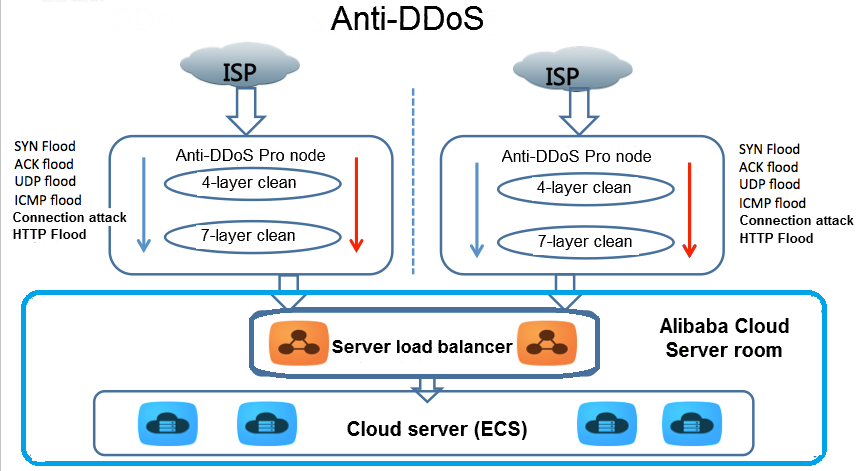
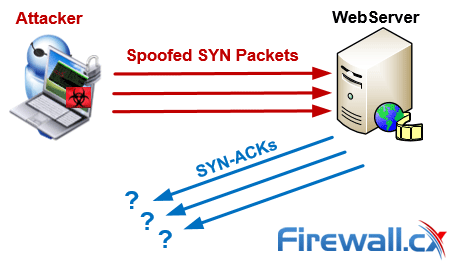
SYN flooding attack detection by TCP handshake anomalies - Bellaïche - 2012 - Security and Communication Networks - Wiley Online Library
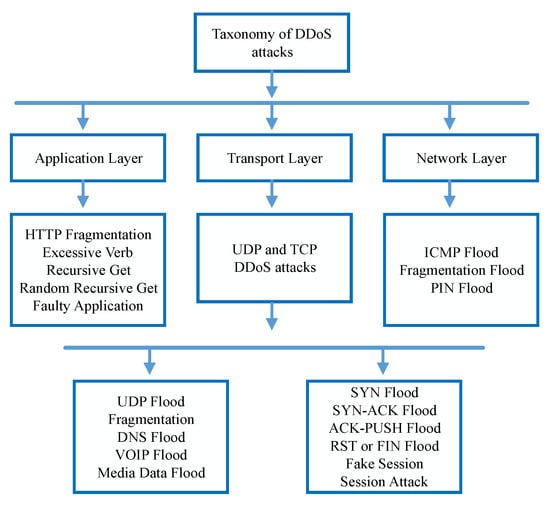
Sensors | Free Full-Text | Adaptive Machine Learning Based Distributed Denial-of-Services Attacks Detection and Mitigation System for SDN-Enabled IoT

Percentage of Successful Transactions During a TCP SYN/ACK Flood Using... | Download Scientific Diagram
Denial of Service (DoS) attack identification and analyse using sniffing technique in the network environment

Percentage of Successful Transactions During a TCP SYN/ACK Flood Using... | Download Scientific Diagram

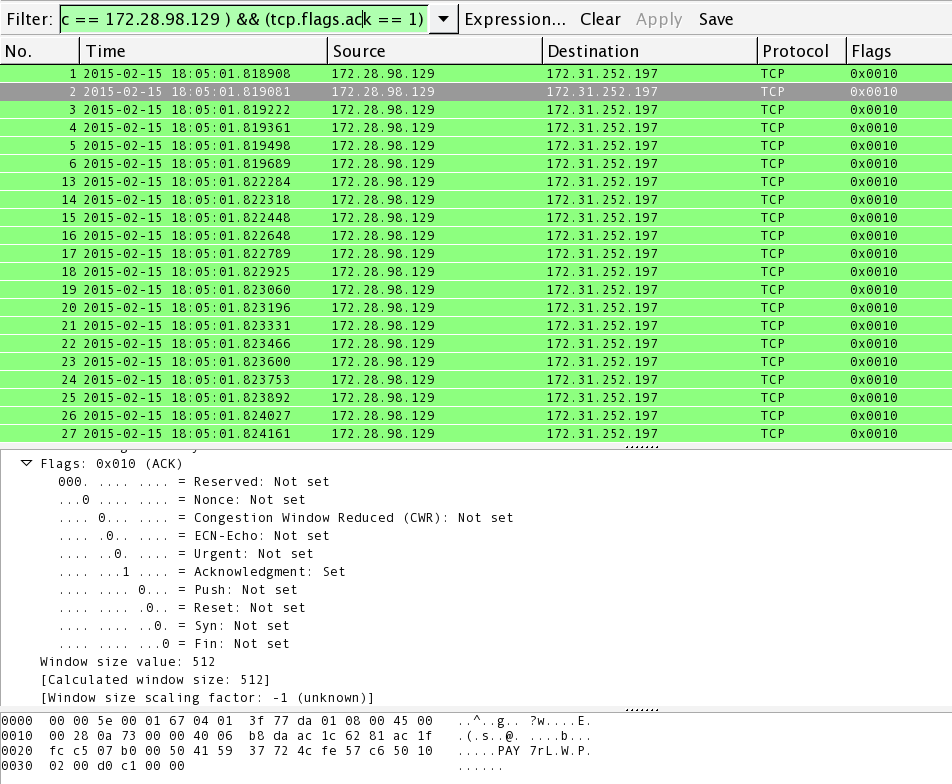

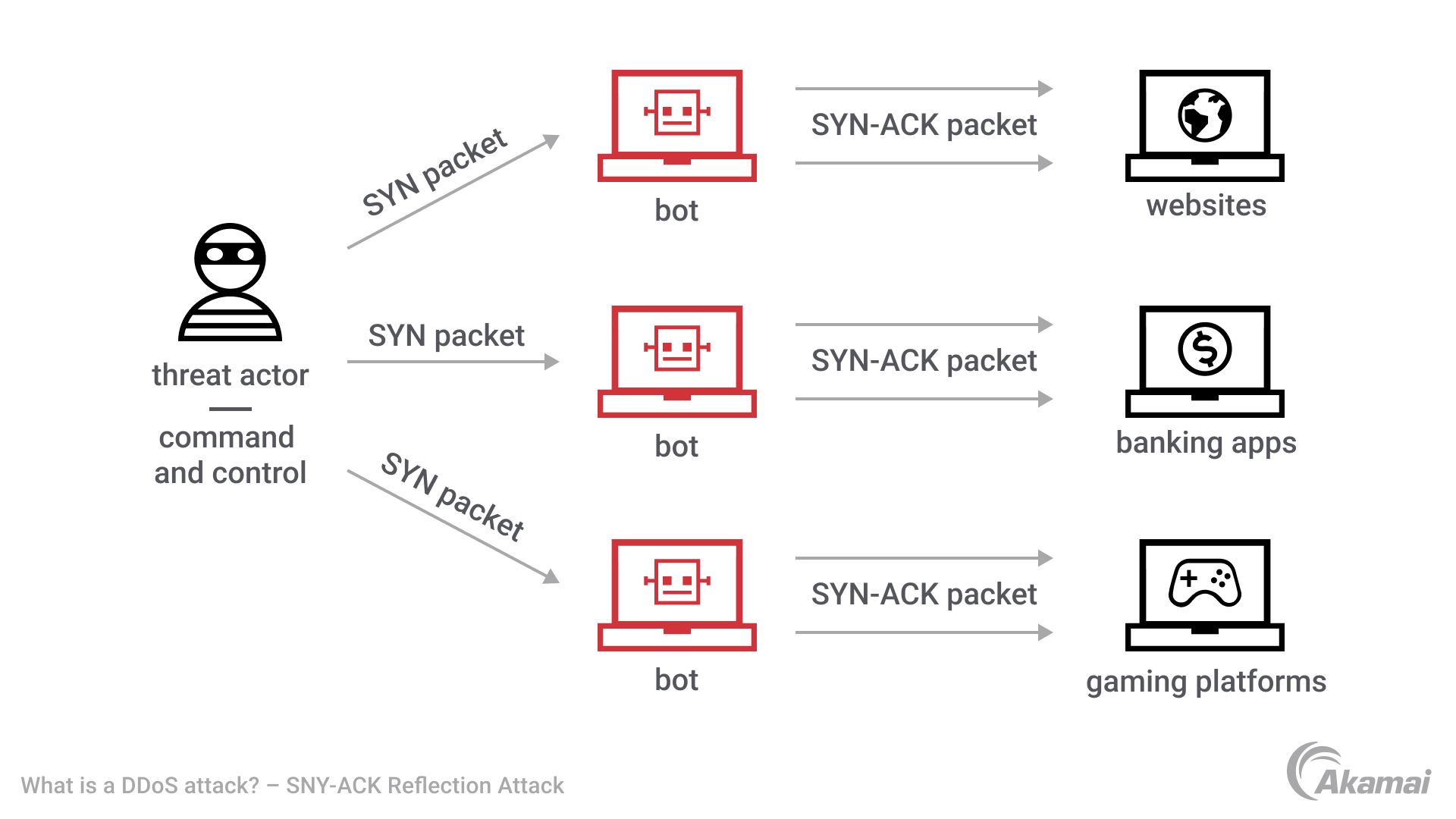

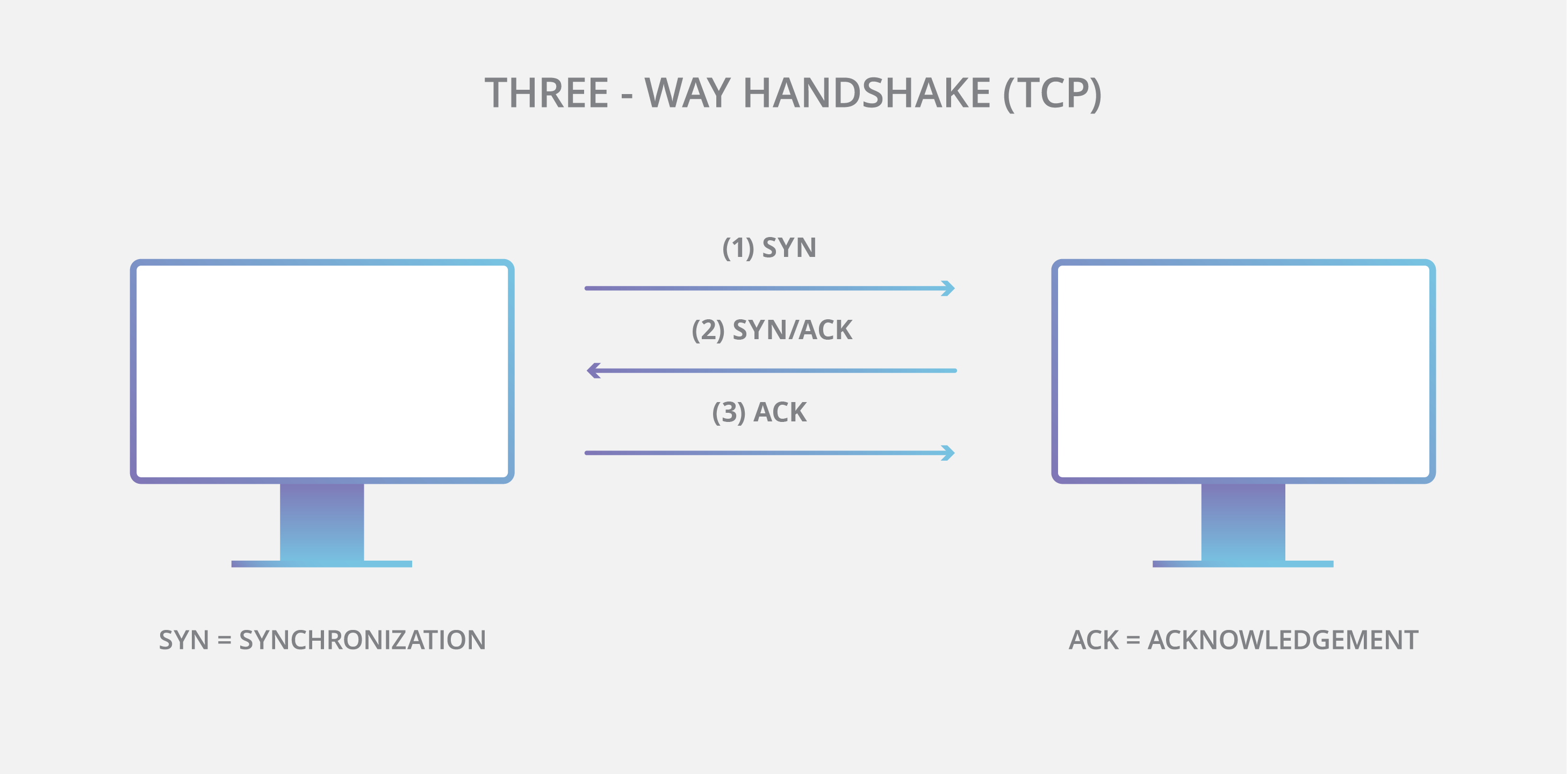


![Real-time DDoS flood attack monitoring and detection (RT-AMD) model for cloud computing [PeerJ] Real-time DDoS flood attack monitoring and detection (RT-AMD) model for cloud computing [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2022/cs-814/1/fig-3-full.png)