Mitigating controls – is this a cure for “all evil” in excessive authorizations risks in SAP? – GRC Advisory

Mitigating controls – is this a cure for “all evil” in excessive authorizations risks in SAP? Part #2/5 – When is it worth creating and when should mitigating controls be avoided? – GRC Advisory

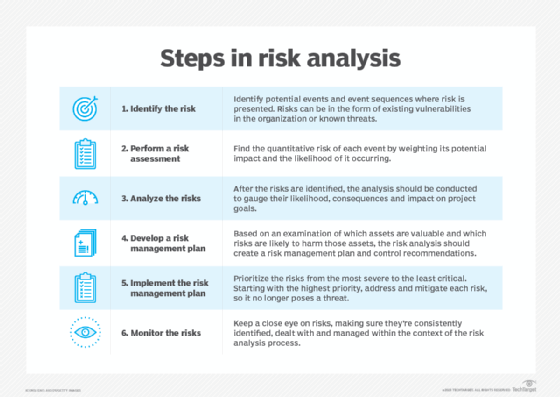

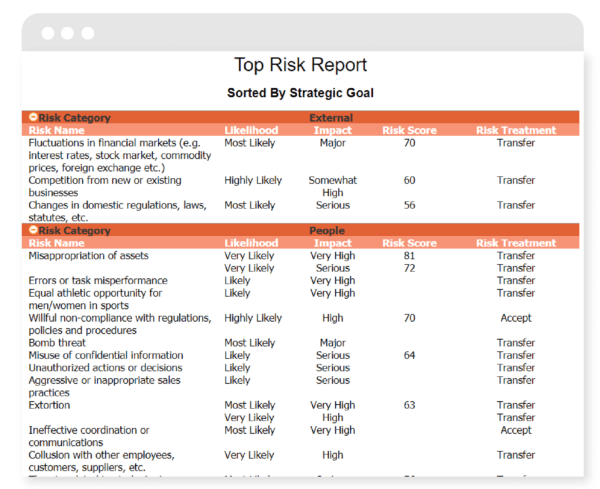

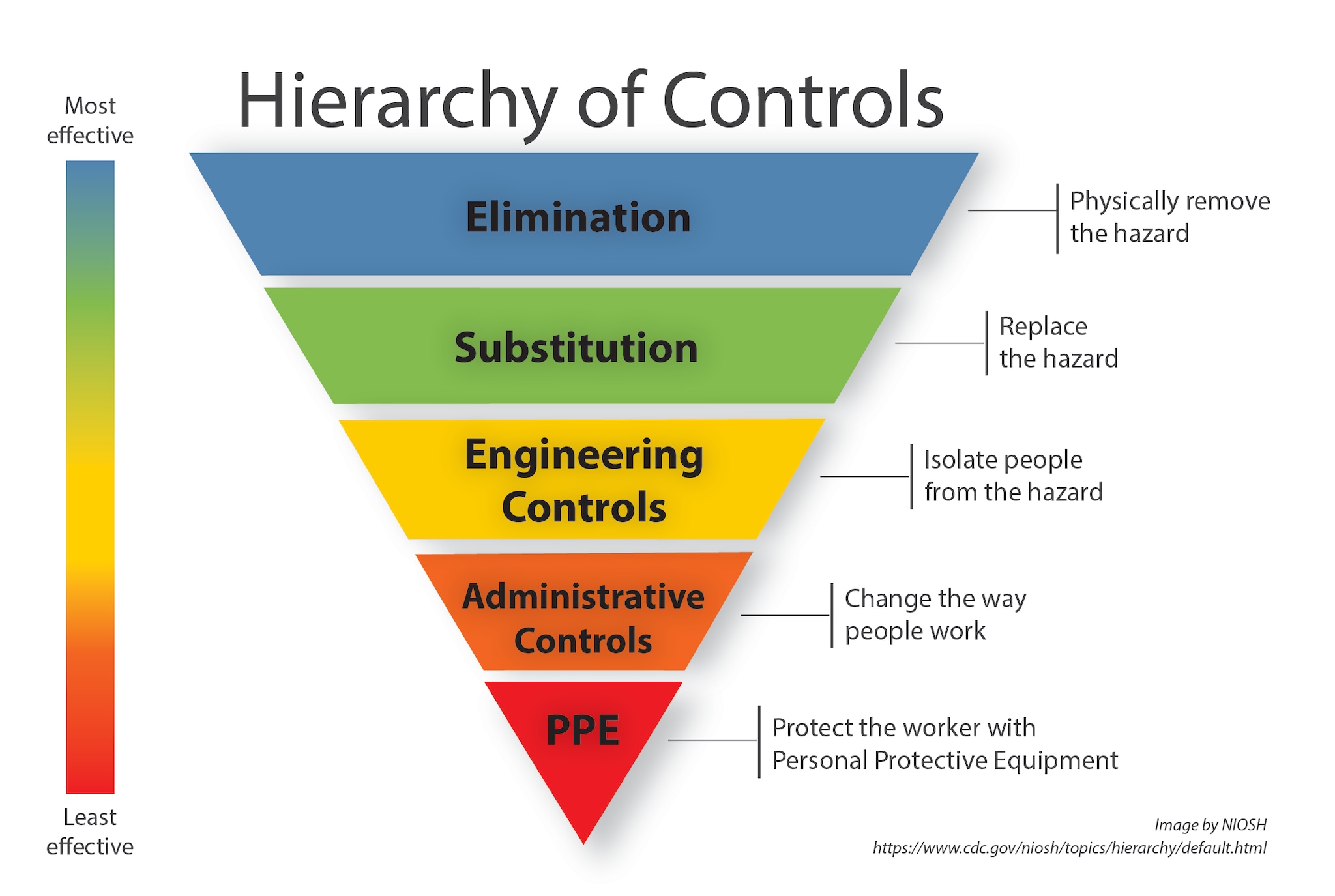




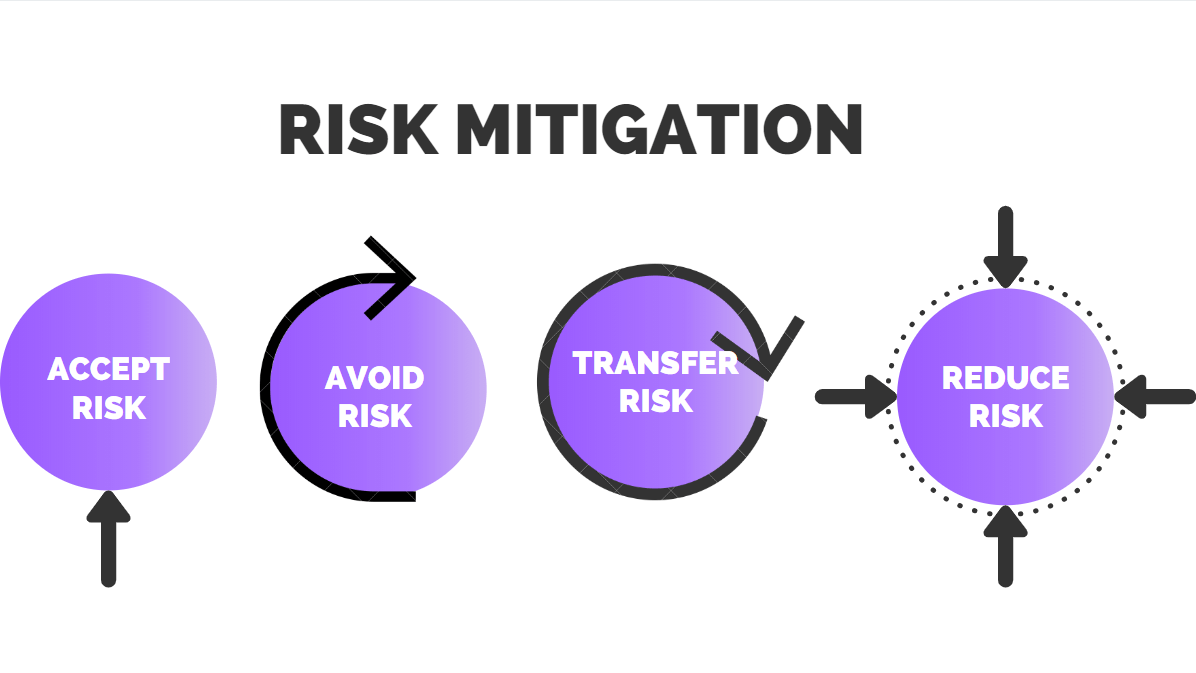



![Infographic] Measure, Mitigate and Monitor Risk Infographic] Measure, Mitigate and Monitor Risk](https://eco-cdn.iqpc.com/gfiles/previews/_8JTcTigrafx_infographic_-_risk_management_0.pdf.jpg)